Executive Summary
The information security management standard ISO 27001 and its guidance standard document ISO 27002 were last updated in 2013. This whitepaper covers new changes in ISO 27002.
However, a new revision of ISO 27002 was published earlier in Feb 2022, and a revised version of ISO 27001 is likely to be published in later this year.
The ISO 27002:2022 is an international standard designed for organizations to use as a reference for implementing and managing information security controls. ISO 27002:2022 was established by the International Organization for Standardization. The standard is intended to be used with ISO 27001, which provides guidance for establishing and maintaining information security management system.
- ISO 27001 provides requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System
- ISO 27002 is a popular, internationally recognized standard of guidance for information security controls.
Changes in New Version of ISO 27002
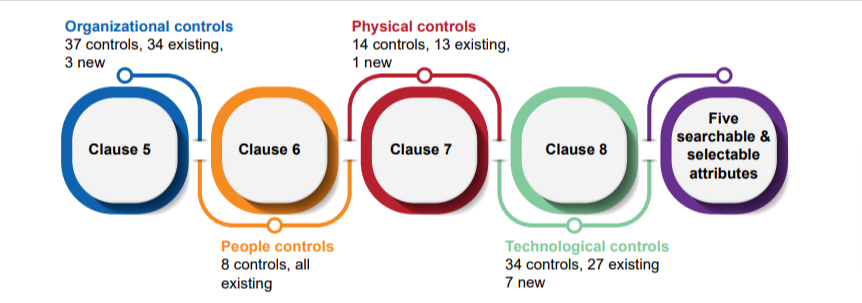
Selectable and Searchable attributes: Control Type, Information Security Property, Cybersecurity Concepts, Operational Capabilities. Organisation can also develop their own control attributes, if required
Highlights of the Changes
The standards are being updated in line with digital transformation and an evolving cyber threat landscape. Controls are revised on risk-based approach that organization possesses.
Previous version has 114 controls and New Version has 93 controls.
The ISO 27001 & ISO 27002 controls are the practices to be implemented to reduce risks to acceptable levels.
New version has reduced the number of controls from 114 to 93. Technological innovations, and an improvement in the perception of how to apply security practices, are the reasons for the change in the number of controls.
Elements of Control
Every control in the new version of ISO 27002 has two new elements in its structure:
- Attribute table: A table describing the set of attributes associated with the control
- Objective: Rationale for applying the control, i.e., why a control needs to be implemented. (e.g., to ensure confidentiality, integrity etc.)
Controls attributes
The change that brings the added value for this new version of the standard, as it provides a uniform way to sort controls against different criteria.
Attributes for every control are as follows:
- Control Types: Preventive, Detective, and Corrective.
- Information Security Properties: Confidentiality, Integrity, and Availability
- Cybersecurity Concepts: Identify, Protect, Detect, Respond, and Recover.
- Operational Capabilities: Governance, Asset management, Information protection, Human resource security, Physical security, System and network security, Application security, Secure configuration, Identity and access management, Threat and vulnerability management, Continuity, Supplier relationships security, Legal and compliance, Information security event management, and Information security assurance.
- Security Domains: Governance and ecosystem, Protection, Defense, and Resilience.
These attributes will help to make it easier and understand which controls are applicable according to criteria relevant to the business (i.e., not related only to information security management system of the organization), as well as the integration of ISO 27002 controls to other similar security frameworks, like NIST Risk Management Framework.
Information Security Management System
An information security management system (ISMS) defines policies and procedures to comply, manage, control, and continuously improve information security of the organization. Systematic approach of ISMS including processes, technology people and premises helps you protect and manage business information of the organization.
Details of new and renamed controls
Following are the details of the newly added 11 controls and 23 controls that have been renamed:
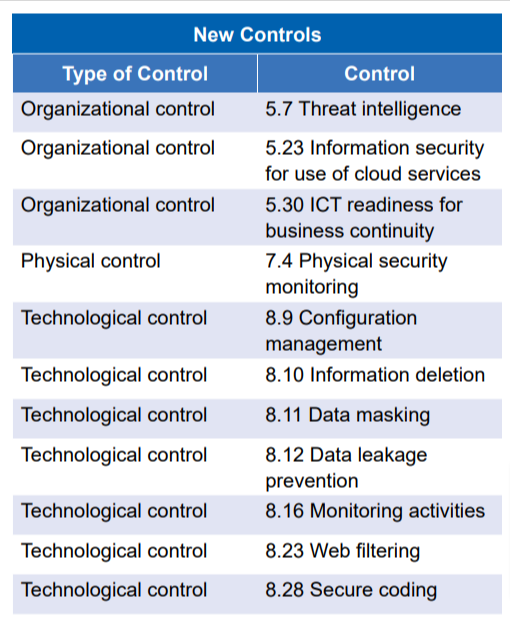
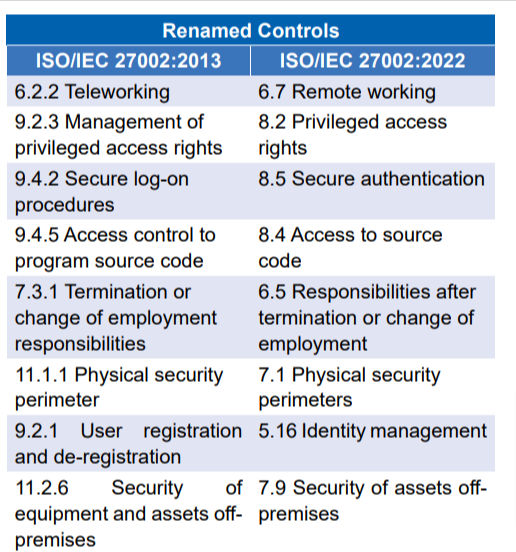
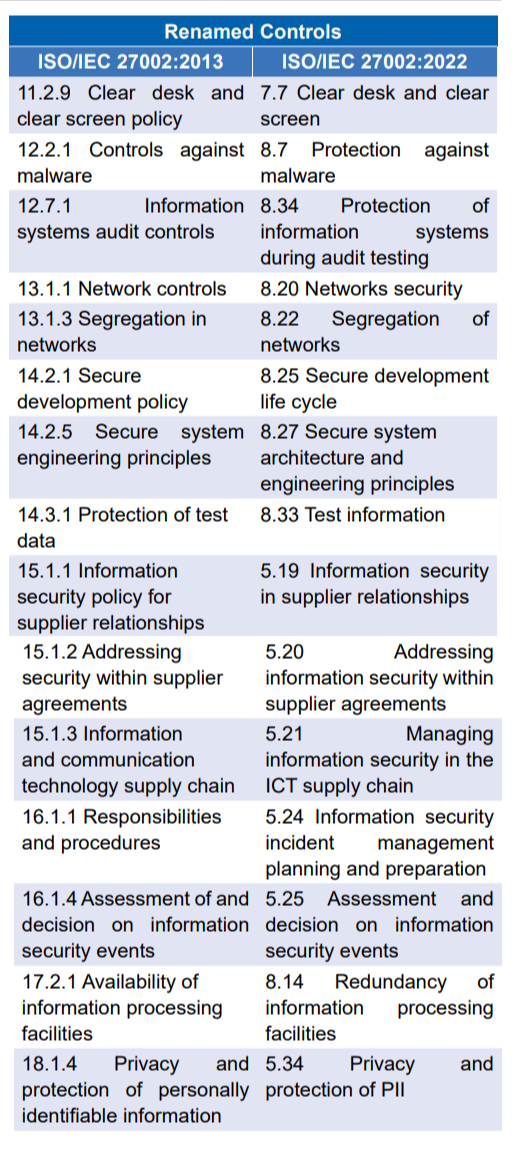
These changes that are listed above will help keep the focus on information security aspects of processes and activities, reducing the effort for implementing and maintaining the Information Security Management System.Given below are the next steps for the organizations to address newly introduced controls.
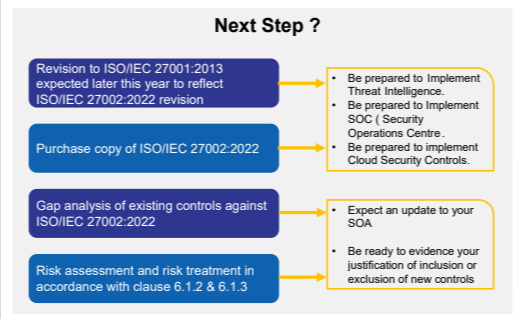
Establish a robust and secure approach to Information Security
Coforge supports organizations in effectively implementing and assessing the readiness of ISO 27001 / ISO 27002 compliance, risk assessment through an end-to-end lifecycle. Our approach allows organizations to manage information security risks in their organization and whilst enabling them to achieve their business objectives in a controlled and secure way. We help organizations to develop and implement best practice policies and procedures through our tailored evidenced based approach.
Information risk governance
Information risk governance gives you the assurance that risk-based decisions are logical and valid and made in a timely manner.
Information risk management enables organizations to balance unacceptable business exposure to risk with the implementation of restricted controls which may prevent the business.
Our consultants provide practical information risk management and governance capability. They consider a range of risk and governance options to ensure the most suitable approach is provided to fit your organization’s needs
Information security assessment methodology
We follow three step methodology that helps us decide the most suitable approach:
Step 1 - review all relevant governance factors of your organization and providing readiness or compliance report based on the scope, objective, criteria, and the context:
Internal context
- Organizations Strategic goals and objectives
- Structure of the organization
- Specific Roles and responsibilities of key risk management stakeholders
- Your existing risk management processes and procedures
- Existing risk management policies and procedures
External context
- Your legal, regulatory, and contractual compliance requirements
- Competitive environment of your business
Step 2 – Utilizing the identified internal and external governance details and recommendations of the assessments, we help your organization to define and deliver a structure for information risk governance, including:
- Defined criteria for risk analysis and escalation
- Defined reporting and structures
- Formal allocation of roles and responsibilities of your organization
- Development of meaningful KPIs which fits for reducing cyber risks.
- Risk management policies and procedures
- Risk assessment templates
- Risk register
- Advice on best-in-class tools
Step 3 – Coforge consultants provide ongoing support throughout the governance process, including creating, reviewing, or improving the risk directive committee and structures, reporting lines and communications required for effective information risk governance and ensuring that risk is being managed in line with the agreed criteria with the organization.
Addressing New Control Requirements
Coforge offers industry recognized and effective tools to achieve intended outcome. The tools which can provide you proven outcome to support standard compliances but not limited to SIMP (Security Incident Management Platform), iDART (Intelligent Detection & Response of Threats) and MASTER (Managed Automated Security Testing & Enhanced Remediation)
